Back to Blue Team
Kubernetes Defense
Prerequisite
- Experience establishing security controls for Kubernetes clusters
Challenge
Online retailer Flotsam, Inc., is reeling from the results of a recent penetration test of their new Kubernetes cluster in which their sample customer data was completely compromised. You have been hired to develop new security controls to better harden the company’s Kubernetes platform and its workloads. Your point of contact has provided the cluster diagram and key details in the platform section below.
The Platform
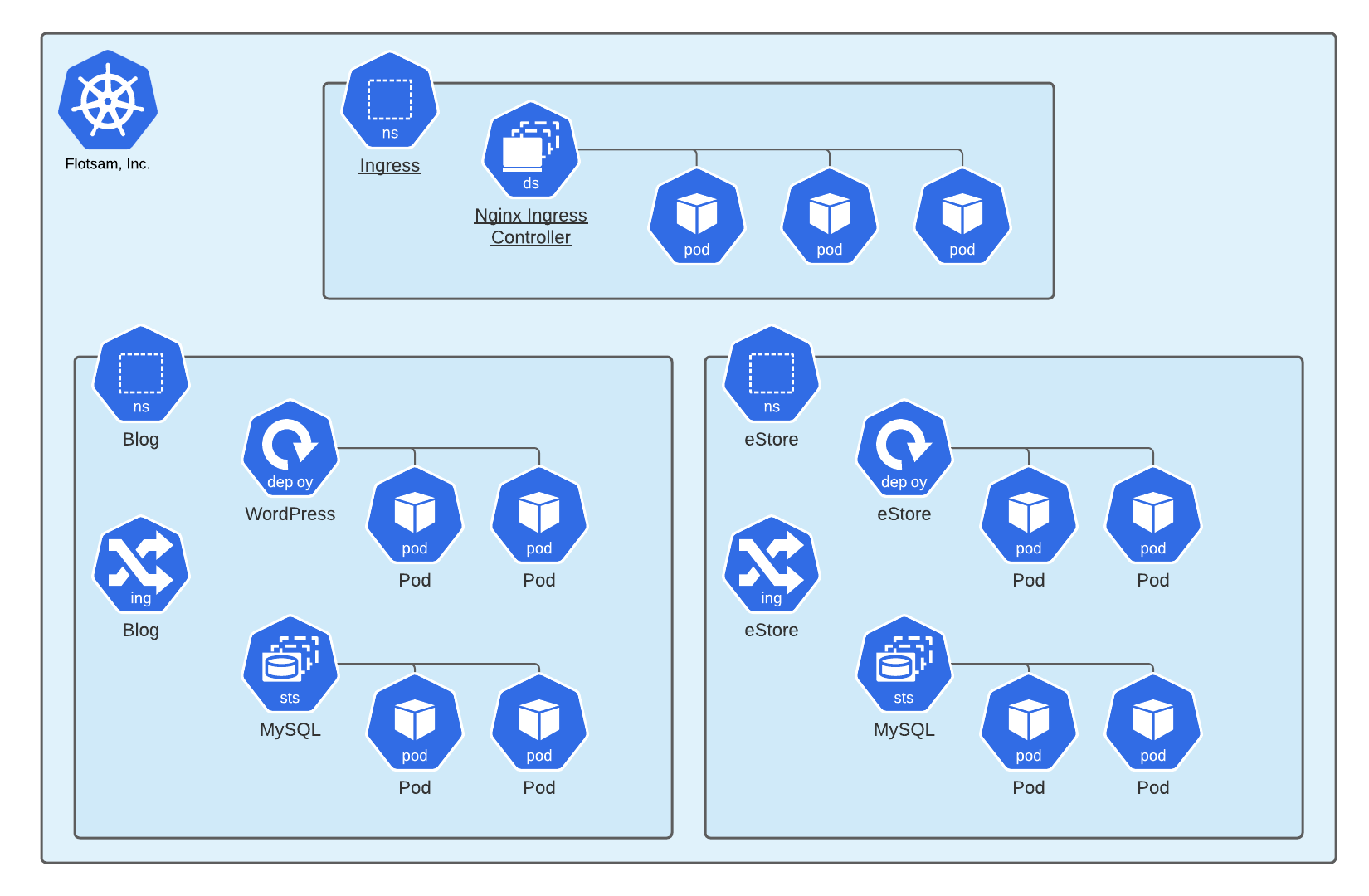
- The marketing department maintains a WordPress blog that includes a custom theme and a handful of plugins for SEO, metrics, etc. The WordPress container image is the official image from Docker Hub. A CI/CD pipeline monitors Docker Hub for new images and initiates a new build and release whenever a new image is published.
- The ecommerce team maintains an internally developed shopping site that is Flotsam’s primary source of revenue. The site is a handful of JavaEE applications that are in the process of being refactored as a cloud-native application. Previously, the applications were bundled into WARs and deployed to an HA pair of Tomcat clusters. As an initial stage of migrating to Kubernetes, the SREs have added the WARs to an OCI image based on the official Tomcat image from Docker Hub. The Java development teams are not familiar with Kubernetes, but they are otherwise very senior developers and previous penetration tests have not identified significant issues with their applications.
- The ecommerce databases store customer PII, including credit card numbers, and Flotsam’s primary concern is protecting customer data.
Requirements
- Consider the platform’s threat model. What managerial, operational, and technical controls are required to harden and protect the platform?
- The initial scenario is intentionally generalized, so when specific details are required, make a reasonable choice and add it to your scenario (e.g., is the cluster on-prem, EKS, or GKE?). Given the technical details you add to the scenario, what specific implementations would you choose to meet each of the operational and technical controls you have defined?
- The scope of this challenge is limited to the Kubernetes cluster, so feel free to make reasonable assumptions about existing security controls and policies that can be referenced (e.g., access control policies, etc.).
Deliverable
- A draft security policy titled “Kubernetes Cluster Security Controls”. The policy is a draft, so do not feel you need to spend time working on your prose. Instead, focus on the breadth of the policy and providing 3–4 sentences for each section describing what should be in the final version.
- A description of the specific technical solutions you would implement in Flotsam’s cluster to meet the operational and technical controls you have identified.
- Good cybersecurity takes a team, and there is no expectation that each team member have every skill that the team as a whole requires. Feel free to focus more on whichever deliverable is more comfortable for you, but please do provide both deliverables.